Tuesday, May 22, 2007
Everything is completed and handed in for marking. The only thing left now is a presentation i wish to present with regards to my study into Internet Censorship in China, which I will record and post on-line. I ask those interested to please click on the link 'May you come to the attention of those in authority' to view my weblog on the issue.
I would like to thank Stuart, Simon and everyone on the course for the last few months and look forward to the design show in a few days.
Friday, March 09, 2007
‘Online Dental Technology Community’
Introduction
‘I have the intention to develop and establish an on-line Dental technology Community. The idea is to allow like-minded individuals within the Dental Technology Field (Professionals, Academics & Students) to share resources & knowledge. As the community grows it will allow Students to find relevant information for their assignments and help keep Professionals at the fore front of their field.’
Background – Key Changes
The field of Dental Technology is rapidly changing and evolving. The number of universities in
Development
My girlfriend, along with several friends are all Dental Technicians. I know from their experiences that there is a lack of Information & communication available on the World Wide Web and amongst their peers.
Furthermore, I became aware that on Wednesday (21/02/2007) Jeffery Lewis, Senior Lecturer & Head of Dental Technology at
After having a meeting with Jeff, It is now my intention to work with several members of the
Research – Web 2.0
After searching through a large array of websites, Wikia communities proved to be the most appropriate source to draw inspiration from. Some of the features I found to be particularly useful & would appeal to it’s users include -
• Free Community support
• Freely licensed content
• File upload features allows to upload graphics or sound files
• Easy to edit, promoting user interaction.
• Customizable site style and navigation, promoting individuality.
• Databases download available so your data can never be locked into the site, ensuring the information remains free to the user.
• Completely open site. No annoying hidden pages or login required. Meaning the site is user friendly & encourages browsing of resources.
WHY would people want to use this particular technology?
Users & Contributors to online communities are motivated by –
• The information they can obtain.
• Increased reputation and a sense of having an effect, as well as a sense of community.
WHAT would they want to do with the technology?
An online community would allow those within the field to –
• Discuss & exchange information with ease.
• Listen to Pod-casts.
• Stream Videos.
• Acquire contacts. Bring students, academics & professionals closer together.
Initial Contacts
• Jeff Lewis
Head of Centre for Dental Technology, UWIC,
• Chris Maryan
Head of centre at
• Mark Gilbert
Lecturer at MMU and Chair of BIDST.
Associations Contacted
• Pete Gough, Webmaster
Orthodontic Technicians Association
• Sue Adams, Secretary
Dental Technologists Association
• Claire Poole
Dental Laboratories Association
• Mark Gilbert
British Institute of Dental and Surgical Technologists
P.E.S.T. Analysis
l Political Analysis
Large-scale political decisions and actions have a direct impact on small-scale/individual consumer behavior. As a recent example, terrorist activity and overseas conflict have had an obvious impact on worldwide tourism.
A recent change in the law now means that Dental Technicians have to be qualified and registered with the British Dental Association. Therefore more institutions will have to teach Dental Technology to Degree standard again.
Furthermore, there need within the field for better communication.
l Economic Analysis
The rise and fall of any economy is cyclical, and will always affect different sections of public life in different ways.
Despite the drive for big profits in technology, there is a counter movement that is making software and hardware more accessible to the user ‘Virtual communities.’ Various online media (i.e. Wikis, Blogs, Chat rooms, Internet forums, Electronic mailing lists) are becoming ever greater knowledge-sharing resources. Many of these communities are highly cooperative and establish their own unique culture. They also involve significant time from contributors with no monetary gain.
l Social Analysis
Websites such as Wikia, Blogger, Myspace do not deliver services in a vacuum. They are social phenomena which provide important focus for different communities, individuals, institutions, organizations, businesses and so on. Large-scale social trends such as the Open Source Initiative provide a significant opportunity for audience participation & sharing of information. Awareness of these developments, and the ability to tailor services to address them, is an important factor in the sustainability of my product.
l Technological Analysis
New media, and particularly the Internet, have had a dramatic impact on consumer behavior and expectation. Users and visitors expect to be able to interact with an organization remotely, and often look to libraries, archives and universities to extend their real-world credibility and service provision into the digital domain.
The other major impact of new media in this context is the way in which information is increasingly being delivered in bite-sized pieces. As the pace of technological change increases and the channels of content grow exponentially, consumers are less willing to engage with in-depth or academic research into a single subject. All of these factors will have an influence both on the delivery of my final product and on the ways in which it is marketed.
Future Development
I fully intend to design & develop this project all the way to a finished product. However, as the project deadline is Friday 09/03/2007, I will have to return to this project at a later date. Below is a list of the next steps I need to take in developing the online community -
• Develop questionnaires to be sent out to all those concerned to help obtain an understanding of what features (such as Pod-casts, Videos, Question/ Answer sections etc) users would find most useful.
• Decide which software or website would be the best place to host the community.
• Further promote the community & find other initial contributors and administrators.
• Create a
A Fable for all Dental Technicians








References & Useful Websites
Wikipedia - Virtual community
http://en.wikipedia.org/wiki/Online_community
Wikipedia - Podcasts
http://en.wikipedia.org/wiki/Podcasts
Wikia Communities http://www.wikia.com/
Orthodontic Technicians Association http://www.orthota.co.uk
Dental Technologists Association http://www.dta-uk.org/
Dental Laboratories Association http://www.dla.org.uk/
British
You tube http://youtube.com
Wednesday, January 31, 2007
Research Topic: Free Speech (Internet Censorship )
Abstract
For the purposes of this paper I am going to focus on the issue of free speech, to gain further knowledge for my Dissertation Topic (Internet censorship).
Censorship is the moral or legislative process by which society “agrees” to limit what an individual can do, say, think, or see. All societies have forms of censorship, effective only with sufficient threat and severity of punishment for violating the censorship rule. Historically, the various forms of censorship have predominantly focused on social norms. Clearly, political and religious organizations limit what individuals can do. For example, organized societies censor premeditated murder. Censoring this type of behaviour has universal appeal and arguably increases social welfare because individuals can dedicate more resources to productive activity rather than protecting themselves from every individual with which they interact. This represents a reduction in transaction costs. Furthermore, censorship is often aimed at behaviour that creates negative externalities, which are costs borne by third parties. For example, smoking is an activity that can impose costs on non–smokers, and limits placed on smoking attempt to reduce these costs.
One recent target for censorship by governments across the globe has been the Internet. Censorship of the Internet has focused on a wide range of topics, including pornography, hate speech, and bomb–making instructions. The justification for censorship of such content is that this would lead to a greater social good, even if individuals are limited in what they can consume on the Internet. To date, the Internet censorship movements have taken two predominant forms: limiting what can be viewed or what can be posted on the Internet. It is becoming more practical to limit what can be viewed on the Internet through filtering technology. Today there are numerous Internet filtering programs available, several of which are commercially successful.
Users throughout the world are being blocked from viewing content by Internet Service Providers and being subjected to ever more governmental approvals. For example, China is attempting to restrict political expression, in the name of security and social stability. It requires users of the Internet and electronic mail (e-mail) to register, so that it may monitor their activities. Nevertheless, supporters of Internet censorship continue to press for national legislation limiting what can be posted and viewed on the Internet.
Objectives of the Literature Review
This literature review will be conducted prior to the onset of my study of Internet Censorship and will be used as basic information for formulating the objectives of my dissertation.
Through reading several books and journals, I have been able to acquire a good understanding of the questions and issues people have on the subject. For this paper I intend to categorise the various literature I have read into three sections; For & Against censorship and another section for neutral articles. I will then conclude this paper stating which texts are most convincing and make the greatest contribution to my understanding of the topic.
Those who oppose Censorship
Who Controls the Internet? Illusions of a Borderless World
by Jack Goldsmith and Tim Wu
This book is essentially a number of case studies of the Internet's challenge to governmental rule in the 1990s, and the ensuing battles with governments around the world. We learn of Google's struggles with the French government and Yahoo's capitulation to the Chinese regime; of how the European Union sets privacy standards on the Net for the entire world; and of eBay's struggles with fraud.
The authors argue national governments will continue to maintain their sovereignty in the age of the Internet, largely because of economics: e-businesses-even giants such as Yahoo, Google and eBay-need governmental support in order to function. When Yahoo, an American company, was tried in French court for facilitating the auctioning of Nazi paraphernalia in violation of French law, the company was eventually forced to comply with local laws or risk losing the ability to operate in France. As eBay grew into an Internet powerhouse, its 'feedback' system could not keep up with cunning con artists, so it hired hundreds of fraud prevention specialists (known as 'eBay cops').
The destiny of the Internet over the next decades, argue Goldsmith and Wu, will reflect the interests of powerful nations and the conflicts within and between them. Most controversially, they argue that existing international law has the power to control the Internet.
Cyber Rights: Defending Free Speech in the Digital Age
by Mike Godwin
The author of this book is a former American journalist and now counsel to the Electronic Frontier Foundation, an organization devoted to guarding individual rights in cyberspace. Mike Godwin is an activist who was deeply involved in turning back the threat of regulation and, at least for the time being, securing rights of free expression online.
For several years in the mid-1990s, the constitutional future of the Internet hung in the balance as the American courts debated it‘s future: Would it be treated as a medium of expression meriting the full protection of the First Amendment, or would it be subject to content-restrictive regulation, like broadcasting under the Federal Communications Commission?
This book largely presents Godwin's deep involvement in what he calls the "cyber porn panic" the push to control Internet. One key philosophy that Godwin makes a convincing case for is that policing the Net should be a matter of individual ethics rather than of legislation or prosecutions. Godwin also discusses another interesting concept; of changing peoples mindsets rather than enforcing censorship and regulation.
Those who are in favour of Censorship
There's No Such Thing as Free Speech: And It's a Good Thing Too by Stanley Fish.
Of all the books I read, this was the most controversial. In his book, Stanley Fish suggests that the idea that we have “free speech” is a mirage. To make his point, he redefines free speech not as the right to say what we want to say free from governmental punishment, to a perception of “free speech” meaning speech not tied to any belief system. In addition he describes the concept of free speech as something often used for political or other personal ends.
He argues that the purpose of speech is to persuade, because if we speak, it is to put our views forth. He then extends this idea to “we are for this, which means we are against that…” (p. 367). Because people often disagree, he agrees with what Justice Holmes said some years ago that “every idea is an incitement to somebody.” Holmes was arguing that just the desire to maintain peace was insufficient reason to curb an individual’s right to free speech, because someone somewhere would be offended by virtually anything that could be said by another person.
However, Fish also notes that there are occasional curbs on free speech. He does not use the classic example that it not all right to shout “Fire!” in a crowded theatre just to assert one’s right to free speech, because in that instance, the likelihood of panicking others, possibly leading to injuries, is great, and the shouting of “Fire!” when no fire exists has no real personal value.
He notes the difficulties in trying to separate speech from non-verbal action, and in fact we know that things like demonstrations are protected by our right to free speech even if no words are used. He makes the point that there are always limitations on free speech, and that often those limitations are imposed on us by society. He opens his essay with an example of this from English history: John Milton, a writer and poet and someone not wanting his words curbed, spoke out for toleration and free speech. However, he didn’t want Catholics given free speech. Their views were unacceptable and bad for society. The insidious truth hidden in Milton’s view, Fish states, is that there can be no pre-determined list of what is all right or not all right to say: first the person says something, and then it is judged to be so outrageous that it is not protected by free speech. Since Fish views all speech as an attempt to assert a point, then he sees censorship as living hand-in-hand with free speech, and of course any form of censorship curbs free speech.
It could be argued that Fish has unnecessarily complicated the concept of free speech, presumably to persuade people that free speech does not exist. However, the fact that he can challenge the contents of the American Constitution, essentially calling it a lie, seems to demonstrate that we do have free speech, at least on some level. He argues that since religious colleges can censor to some extent what is said on their campus, all colleges should be able to, since all colleges hold beliefs. While this is true, it completely ignores the concept of separation of church and state. In fact, Fish seems to be doing what he accuses others of doing. He is manipulating free speech by redefining it. He has literally had to go to great lengths to attempt to do this: one sentence on p. 373 has 45 words in it. Fish has tried hard, but by demonstrating his right to challenge the American Constitution, he has demonstrated that free speech exists.
Neutral Literature
Beyond Our Control? Confronting the Limits of Our Legal System in the Age of Cyberspace by Stuart Biegel.
Beyond our control examines the state of American law, international law, social norms and technological controls as they relate to the definition of crime in the information age. The book largely offers a descriptive discussion of the many issues that emerge when we begin to apply the law in cyberspace.
The book is divided into three parts. The first section goes on to elaborate the types of problematic behaviours that can be found in cyberspace. These include dangerous conduct, fraudulent conduct, unlawful anarchic conduct, and finally, inappropriate conduct. Each category then details examples ranging from the dangerous conduct of cyber terrorism to the inappropriateness of hate-related websites. Biegel covers the many contemporary controversies surrounding cyberspace - child pornography, harassment, cyber stalking, copyright violations, cyber terrorism, any many more.
Section Two considers how we might go about regulating problematic behaviour in cyberspace. More specifically, examine the laws that have been passed to regulate Internet-related issues and the different regulatory approaches that are being used. Firstly the author relates to the possibility, and problems, of employing a traditional regulation model involving criminal statutes. For an example of a previous problem, the author turns to the issue of distributing child pornography online. Developed in the late 1990s to regulate the distribution of child pornography via the Internet, statutes were met with substantial debate because of their perceived attempts to regulate activities that many in cyberspace considered protected by the First Amendment to the U.S. Constitution. The author argues that any attempt to regulate the Internet using traditional law must consider issues similar to those that doomed the child-pornography legislation, and such statutes will therefore require extensive consideration and planning during the drafting phase.
The second recommendation concerns the use of international models of cooperation. Returning to an earlier discussion concerning the problem of regulating an area that is not bound by physical boundaries, the author argues that a possible solution could lie in drafting legislation that is enforceable around the globe. Of course, while this seems like a valid solution, even Biegel is quick to point out that there are several problems that could develop from an attempt to regulate cyberspace using international standards and regulations. For example, any attempt to regulate pornography will certainly be faced with the question of what is pornographic, as definitions of pornography must consider which country's definition of pornography is to be accepted. The drafting of this legislation will require an extensive examination of custom and international law. While not impossible, the author concedes that the use of this approach will likely require consideration of the perspectives of officials of countries other than the United States.
The final recommendation deviates from a discussion of the law and instead focuses on the use of code-based regulation. Here, regulation of cyberspace would be enacted by modifying the protocols through which users connect to cyberspace. It has long been accepted that the Internet was not designed with security in mind, and there have been arguments in the past concerning a change to the Internet's technological-security structure. The work of Internet law scholar Lawrence Lessig is referenced in this section, as Lessig has argued in the past that code-based regulation is perhaps the easiest method of regulating criminal activity on the Internet. Biegel, however, recognises that there are problems with solely relying on code-based regulation. First and foremost is the fact that users have historically been successful at circumventing such protections. The question remains as to whether the costly use of code-based regulation would provide an adequate response to the problem, or merely a temporary solution as users modify their approaches to Internet-based crime.
The final section of the book takes the types of regulation that are possible and an example of each type of problematic conduct detailed in the first part of the book and attempts to examine how the law can be used to better regulate cyberspace. He then describes how concepts already present in American law, regulations available at the International level, and changes in the computer code that construct the Internet can be used to regulate this problem. As the argument moves from problematic behaviour where relative consensus exists, such as terrorism, to behaviour where less consensus on the level of crime actually exists, Biegel attempts to note that defining a "crime" is very much a political process.
As a conclusion, Biegel lists a series of "regulatory principles" that emerge from the book. He argues that, "this book takes the position that regulation is a neutral term, and that in a vacuum it should be viewed as neither a curse nor a panacea" (p.356).
Conclusion
While conducting this paper I only used completed articles in book form, no partial articles off the internet that could be bias or have false information. Also, a large proportion of literature read was American and further research will be needed for me to gain a clearer understanding of the global issues of this topic.
The two books I found most useful while conducting this paper were There's No Such Thing as Free Speech: And It's a Good Thing Too by Stanley Fish and Beyond Our Control? Confronting the Limits of Our Legal System in the Age of Cyberspace by Stuart Biegel. Both these books required me to read them in their entirety to gain a true appreciation of the themes and issues they presented.
Through conducting this paper, I have learned much invaluable information. I now have a good understanding of the general groups of people in favour of and opposed too internet censorship. I am now aware that those with kids, who are married, who are older, who use the internet for religious content, who work in the public sector, and who think pornography or privacy are the predominant issue concerning the Internet tend to favour Internet censorship.
On the other hand, those who are male, live in urban environs, use the Internet for political content, have more Internet experience, are more comfortable on the Internet, work in information industries, and who feel government regulation or censorship is the most important issue concerning the Internet tend to be against Internet censorship.
I also now have a fairly good basic understanding of the issues for and against censorship of material. Having learned that the major problem governments face is the lack of physical boundaries, making it difficult to determine where violations of the law should be prosecuted. Furthermore, I have become aware that many people are strongly opinionated on this issue, yet few base their understanding on fact or sound thinking. For example, many people feel that Internet content regulation should become International. However, given the diversity of cultures that exists throughout the globe, it would be impractical for a set of International laws to exist that every individual country should adhere too. Never mind the costs and difficulties governments would face having to enforce such laws. An alternative idea is Internet content regulation based on the cultures of each country, although this would more than likely lead to a totalitarian internet, comprising of numerous highly monitored policed states.
Reference
Biegel S. 2001, Beyond Our Control? Confronting the Limits of Our Legal System in the Age of Cyberspace, The MIT Press.
Fish S. 1994, There's No Such Thing as Free Speech: And It's a Good Thing Too, Oxford University Press.
Godwin M. 2003, Cyber Rights: Defending Free Speech in the Digital Age,
The MIT Press; Rev Update edition.
Goldsmith J. & Wu T. 2006, Who Controls the Internet? Illusions of a Borderless World. Oxford University Press, USA.
Bibliography
Bollinger L.C. 2003, Vigilant: Free Speech in the Modern Era,
University Of Chicago Press; New Ed edition,
Coatgate C. 1996, The Internet and the Issue of Censorship,
Cardiff Institute of Higher education, Colchester Avenue.
Isenberg D. 2002,Guide to Internet Law, Random House Trade Paperbacks.
Levinson N. 2006, Free Speech Stories, University of California Press.
Peng Hwa Ang, 1997, How Countries Are Regulating Internet Content,
Nanyang Technological University, Singapore.
Reading a Research Paper
Smart or Intelligent Clothing are articles of clothing, footwear or accessories that feature micro-electronic sensors which gather, communicate and output usage and performance data. Electronic sensing and computing technology is integrated into clothing with minimal to no visual indicators of the technology.
“Electronics and fashion experts agree that Smart Clothing represents the future of the two areas” (Baurley, 2003). But at present, limited fashion and high prices mean Smart clothes are a small niche market.
What is the motivation for the work (commercial, exploratory, educational)?
The research paper I decided to analyses is called “Optimizing Multidisciplinary Contributions for the Smart Clothing Development Process.” This paper focuses on how to achieve a greater integration of electronic technology and fashion design, so more fully integrated designs can be realised. The paper goes about this by conducting Background Research; which comprises of a literature review, lessons learned from previous projects & a series of interviews with key professionals.
In the Literature review, it is explained that there is a need to improve profitability in order to cover the development costs. This means in order “to gain social acceptance, a new design strategy is required (Edwards, 2003). Therefore in the field of Smart Clothing, the ability to shift perception and break from the past is critical for a radical innovation.
Designers must break the ‘pre-existing pattern,’ or what is also known as the Creative boundary. De Bono (2000) explains that “All information is perceived, recognised, analyzed and organised due to the ‘routine perception track’ which was set up by previous experiences. The brain can only see what it is prepared to see.” In this manner, all information, no matter how new or old, is explained by the known theory and fashioned to support that theory. In order to breakthrough the existing boundary, a new perspective is required.
This point is emphasised in the summary of lessons from previous projects, where a researched worked with two supervisors from both fields (electronics & fashion). The final result was a far from integrated design, with the problem lying in finding symmetry between fashion expression and a functional approach. In this instance it was difficult for one person to balance the inputs from two areas, it must be even harder for multidisciplinary teams.
Concluding the background research is a series of interviews with ten interviewees, who were chosen based on their experience & expertise. Here it was noted that problems occurred with communication and a language barrier exists between the two fields. Furthermore, proximity between both fields is important. Having all required disciplines in one place allows a quick response to any problems that might arise.
The background research concluded that a fully integrated application was required to improve commercial potential. The extended study revealed that the current barrier was caused by established approaches and procedures.
What is the proposed solution (hypothesis, idea, design)?
Having identified several key issues in the Smart Clothing Development Process, the paper then goes on to formulate a practical method to address three issues: 1) How to achieve the optimum balanced contributions from all the participants; 2) How to integrate the differences of fashion design and electronics technology; and 3) overcome the creative boundary and create an integrated result.
This solution is formulated and expanded through the use of two case studies that were shown to break through the creative boundary, optimize multidisciplinary contributions and integrate the difference of high-tech and fashion sectors. Performance Sportswear & Smart Car (originally a collaboration between SMH & Mercedes Benz AG) were the two companies chosen.
Furthermore, interviews between two sportswear design educators, one sportswear design researcher & one member of the Swatch Product Management Department also took place. Finally, to establish even more clarity, a focus group which comprised of five product designers and another with five fashion designers also took place.
To analyse the information collected from the case studies & focus groups and to obligingly offer some answers to the three issues previously stated, the researcher used grounded theory methods. This involved deconstructing the information into categories in order to extrapolate the key issues, which are then reconstructed to provide new meaning and information. The information is thusly dissected by two methods ‘open coding’ and ‘axial coding,‘ before being reconstructed with all it’s potentially useful information being realised.
What evaluation of the proposed solution is presented?
The proposed solution is a series of strategies that should be adopted to optimize multidisciplinary contributions and help achieve more integrated products. These strategies are as follows:
1. Develop a clear goal & describe how multiple perspectives are evenly incorporated
2. Identify user requirements and clarify how multidisciplinary expertise can satisfy these needs.
3. Develop a context of the new product accordingly and ensure that every participant understands.
4. Define expected contributions of all the participants and establish the basis for a collaborative project.
5. Create a new framework based on the product context to encourage developers to think through and express their ideas in an integrated manner. In this way, fashion elements and technologies cannot be separated.
6. The new framework can be adopted by working closely with others. However, it is important that all disciplines challenge their established procedure and explore the new direction identified.
Did this evaluation convince you of the merit of the proposed solution?
The paper set forth to formulate a practical method to address three issues. A very strategic approach was adopted when collecting the vast array of data and analysing it. The proposed solutions have been carefully developed & I believe offer feasible solutions for the issues raised.
What are the paper’s contributions?
This paper has helped to identify several key strategies, providing a new framework for developers to work with. Firstly It identified several key issues in Smart Clothing Development processes and through a process of research & analysis, went on to introduced several feasible solutions.
What are the future directions for this research?
The next step in the evolution of Smart Clothes is partnership with clothing manufacturers & electronics companies so that items are designed from step one to incorporate and interact with technology. Investigation into what would make smart clothing more commercially viable & how to development the market sector would be a insightful direction for further research.
Versatility is crucial for a mass rollout of smart clothing. The cost of the technology has to come down to the point where it can be incorporated into a person's entire wardrobe, not just one item. Furthermore, fashion is also another consideration as people like to keep up with the latest trends.
The technology has to be easy to access and well integrated into the garment. Furthermore, I assume there must also be consideration about what information will be provide to inform the consumer about exactly he or she is buying.
One further query I have about the future of Smart Clothing is that in terms of data collection and analysis, is there not a possibility that it could become seen as an invasion of privacy?
References
Interactive and Experimental Design in Smart Textile products and Applications; proceedings of International Textile Design and Engineering Conference: Fibrous Assemblies at the Design and Engineering Interface, by Baurley, S. L. [Heriot-Watt University, UK. September 2004].
Wearable Computing Struggles for Social Acceptance; Technology: The Ultimate Fashion Item, by Edward C. [IEE Review. October 2003].
Serious Creativity: Using the Power of Lateral Thinking to Create New ideas, by De Bono, E. [London, Harper Collins Business, 2000].
Bibliography
Busayawan Airdate [Brunel University, UK].
Ray Holland [Brunel University, UK].
David Harrison [Brunel University, UK].
Other Journals read:
Smart Fibres, Fabrics and clothing, by Tao Xiaoping [Cambridge, England. Woodhead Publishing, 2001].
Fashion & Textiles: An Overview, by Gale, Colin, Kaur, Jasbir [Oxford, England. New York Berg Publishers, 2004].
Monday, January 29, 2007
For this brief I was required to visit a real life creative industry company and produce a written web report explaining the company’s production processes. I along with Ian Diez at the end of last year chose to visit a Media Production Company called Boomerang, based at 218 Penarth Road, Cardiff. We met with the Managing director Huw Davies, as well as several other members of the Boomerang Creative team & Production team, to help gain an understanding of the various stages in the company’s design process.
Definition and Planning
It was stated that the first step in a projects life cycle is vital, as the project manager must clearly understand what the client needs and requirements are. By documenting the ideas and concepts of the client’s requirements, the project manger can then create a contract that shows a realistic timescales and budgets for both the client and the production team.
Before creating a contract, the Project Manager must consider the following points-
* Be clear about the clients brief and be aware of what the client’s needs & requirements are. It is important to discuss and clarify unclear information with client.
* Make decisions based on the facts and make an assessment of the risks.
* To be able to understand concerns of members of the team.
* Discuss cost proposal treatment and refer back to client's budget.
* Define resources needed.
* Explain limitations of proposal and make no false promises. It is also important to get a signed agreement to content at each stage of the project.
Information Architecture
Once the project has commenced the company must acquire the relevant information needed for creating the project. Information is generally gathered from the client and if further information is needed the company will allow time for the development team to research and gather the information need for the project.
Design
Boomerang being a Production Company produces television programs for various clients. The company predominately uses story boards to show their clients the design layout, as this is a quick and above all cheap means of conveying ideas before production. Again, a signed agreement is made when agreeing on the design and ideas for the project. When it comes to design they aim to achieve the clients brief, but will say no when something is unachievable.
Construction
This is the production stage of the project where all tasks and the role of the production team has been assigned to each team member. Tasks tend to be set out on a timeline, calendar or white board where team members have a certain amount of time to complete that task before moving on to the next. When a task is completed, a team member signs that task so the project manager is aware what has been completed and what has not. Furthermore, if team members have problems they can also use the timeline, calendar or white board to report any problems to the rest of the team and the project manager.
Marketing
It was stated that a good client relationship is invaluable for acquiring contracts. By creating good contacts, finishing projects on time and by achieving the data for the projects in an orderly manner, all of these factors can influence a client to return for more contracts in the future.
Tracking, Evaluation and Maintenance
Once the project is complete by the production team, the project manager must present the finished project to the client. A final signed agreement is made, as well as discussing with the client if they need the company to maintain the project. Once the client is pleased with the project, it is then common practice for the project to be archived and all documentation from the project is filed away. Archiving properly at the end of each project can have many benefits for the company. The main benefit is that if the client was to return and wanted more work done, then the relevant information is stored and easy to obtain. Boomerang being a Production Company keep Master Tapes of productions, but all other tapes are wiped & re-used.
Analysing the various stages in Boomerang’s Production Processes using England and Finney’s Project Life Cycle guidelines
Scoping the project
‘What is it all about and what is going to be needed?’
Boomerang distinguishes an idea for a potential show and then prepares a pitch to a potential client. This is a potentially risky strategy, as it is not guaranteed the client will accept the pitch.
Proposal
Boomerang propose an idea to a potential client before they develop or plan the project, as it is not guaranteed the client will accept the pitch.
If a pitch is successful, the next stage is to draw up plans such as production schedules and costs, before then preparing a contract.
Contract
Contracts are drawn up after a client has accepted the idea; Boomerang has little control over the terms of the contract as the client can easily decide not to use their idea.
Personnel
Boomerang’s personnel include many people they privately employ. The company also employs freelance workers when needed to deal with specialist tasks and when there is a over-flow of work.
Assets
They use different technology for filming and editing and a number of different programs including a software package called Movie Magic which helps design production plans.
Testing
Testing can only be done once a television episode has been made using a test audience which means it is hard to keep the client updated throughout production.
Final Sign off
Once the project is signed off the company archives the production tapes, before moving onto their next project. The only reason for them to keep in touch with the client is if the client wants to pursue further work with the company.
Monday, December 11, 2006

Production Processes Brief One
The Company i am looking at is a Media Production Company called Boomernag, based at 218 Penarth Road Cardiff . Initialy established in 1994, the Boomerang group has grown to become one of the most successful media production companies in Wales. Boomerang is most known for producing entertainment, extreme sports, factual, musical, as well as radio programming; producing work for S4C, ITV, BBC, Channel 4, Channel 5 and Sky Sports to name but a few. A recent acquisition between two local production companies Fflic and Alfresco, has expanded Boomerang's talent base considerably. This means the compamy now also produces programmes for genres such as children's, lifestyle, comedy, drama and documentary.
I now intend to analyse the companys website, http://www.boomerang.tv/ I intend to assess how well the web-site is designed visualy and determine if the written content on the website is appropriate.

What are the major strengths and/or limitations of the way the information has been organised?
Boomerang's website is presented as a simple html site. It is much more heavy in written content than visual, though simple text and layouts are used throughout. Apart from providing approriate company contact information, the content is clearly provided to give an overview of the work Boomerang develops. Unfortunately apart from describing the programmes the company makes, the lack of visual content makes the site look rather bland. Furthermore, it would be better if more visual examples of the programmes Boomerang produce were included on the site as this would provide greater clarity.
Has the information (text and images) been appropriately edited and structured?
The overall written & visual content is presented in a professional manor. It is clear from the design that the company is aiming to attract high profile clientel. This is done through the use of simple text and layouts. The website is also viewable both in English and Welsh.
Is the hierarchy clear?
The hierarchy of the design is both simple and easy to use. The information is well organised into different categories; about, television, radio, extreme sports and contact. The navigation bar is always situated at the top of the page, with the changing written content appearing below.
Is legibility good?
The legability is good throughout the website. The text is clear and easy to read on the dark background, with the design of the text being designed with a clear font and good size.
Is Readability good?
The readability is good, although a little heavy in places. The language is easy to understand, with no unnessesary termonology that could confuse the reader.
Are images used to give information or just decorate the pages?
The few images used on the pages are mainly there for decoration, however they do relate to the content of the information of the page that they are on.
Is colour used to clarify the information or as an expressive add-on?
The pages are dark blue to tie in with the company logo, with the text written in white. This use of white over a dark background helps to clearly present the information to the viewer, with bold being used to highlight headings and important points.

Friday, November 10, 2006
PERSONAL PROJECT - RESEARCH PAPER PRO FORMA
1. Your general field of enquiry.
I have decided to examine a humanitarian topic which is relevant to us all, ‘freedom of speech.’ Freedom of speech is enshrined in the United Nations Universal Declaration of Human Rights and is granted formal recognition by the laws of most nations. Nonetheless the degree to which the right is upheld in practice varies greatly from one nation to another. In many nations in the developing world strict censorship is enforced, while even among liberal democracies there are different approaches to issues such as hate speech, obscenity and laws.
Freedom of speech is a fundamental principle that provides people with the right to speak their thoughts in public. However, there has been much discussion on this topic lately, especially in the media in light of the 9/11 terrorist attacks in America and the 7/7 attacks in Britain. As a result of these terrorist attacks, both the U.S and U.K governments have introduced new legislation & laws to help combat their war on terror. However, they are not without opposition from those who feel they are impeding on our civil liberties & rights.
Does freedom of speech permit a person to arouse fear or hatred? It is true that freedom of speech can be abused. Nevertheless, this freedom is so important that surely every precaution should be taken to protect those who call upon its guarantee. Freedom of speech continues to be problematic as well as important. I have just read an article where the Ku Klux Klan were given permission to hold a rally in a town in America & received police protection; then they were sent a bill for the additional security. When the Klan protested, the court decided that the group did not have to pay. It is easy to say that the Klan should be silenced because its message is objectionable. However, if one group with objectionable views can be silenced, it soon may become acceptable to silence another group, and then another group. In this light, I am reminded of the Pastor Martin Niemöller famous poem "First they came..." and feel its words & message still ring true today “When they came for me, there was no one left to speak out.”
2. Your chosen subject.
I intend to research & examine the specific issue of Internet Censorship. Internet censorship is control or suppression of material an individual can publish or access on the Internet.The legal issues are similar to offline censorship. One difference is that national borders are more permeable online: residents of a country that bans certain information can find it on websites hosted outside the country. Conversely, attempts by one government to prevent its citizens from seeing certain material can have the effect of restricting foreigners, because the government may take action against Internet sites anywhere in the world, if they host objectionable material.
Total censorship of information on the Internet however is very difficult to achieve due to the underlying distributed technology of the Internet. Data havens (such as Freenet) allow unconditional free speech, as the technology guarantees that material cannot be removed and the author of any information is impossible to link to a physical identity or organization.
However, this does not mean that governmental originations throughout the world are not trying to implement forms of censorship. The recent (September 2004) international operation against the anti-globalization Indy-media network, led to the knock down of several servers worldwide. So this shows that the era of completely free internet is finished. Even in democratic countries the authorities have now the technical and legislative means to shut down anybody on the net, for any good or evil reason. In the United Kingdom, the new Home Office Minister Vernon Coaker set a deadline of the end of 2007 for all Internet Service Providers to implement a “Clean feed” style network level content blocking platform. Currently, the only web sites ISPs are expected to block access to are sites the Internet Watch Foundation has identified as containing images of child abuse. However such a platform is capable of blocking access to any web site added to the list, making it a simple matter to change this policy in future. The Home Office has previously indicated that it has considered requiring ISPs to block access to articles on the web deemed to be “glorifying terrorism”, within the meaning of the new Terrorism Act 2006.
Levels of Internet censorship vary from country to country as previously discussed. Some countries impose stricter regulations and penalties than others. In total there are 61 Cyber dissidents imprisoned to date in various countries for illegal web bloggings and other forms of expression or statements against their governments, with this number ever increasing. In November 2006, governments and companies from all over the world will attend a UN conference to discuss the future of the Internet. This could pen ultimately mean that the face of the Internet as we know it will change. For this reason, I feel it is something that needs to be examined and is in everyone’s best interest that the results are made freely available to the masses.
3. Your objectives. What are you going to document/ uncover/ explain/ question?
In this time of regulation, freedom is really threatened on the Internet. There are peoples who try to monopolize the net, see to censor it, openly or hypocritically, be it is in the name of the defence of the order or in the name of freedom. There are those who agree with censorship, but one is compelled to ask “to what extent?” Denial of inappropriate images of minors for example is something I would hope everyone would see as a good thing. But what about censoring articles with strong religious or political beliefs because the opinions held are not your own? I believe it is imperative that a balance should be reached between censorship of explicit material and freedom of speech.
I wish to obtain an understanding of the current state of affairs throughout the globe in this issue. Firstly I must discover what forms of expression on the internet are under attack. I then intend to examine how special governmental bodies and interest groups suppress the right to free speech on the internet by attempting to silence anyone whose opinions do not conform with their agendas. After I discover what means are used to suppress free speech (e.g. smart filter, websense), I wish then to develop my project further by looking at what tools are available (e.g. Freenet) to help protect those who do not have the fundamental right of free speech..
Having done all this, I intend to present my findings in a professional journal. I am currently looking for an appropriate place for publication among organisations such as Amnesty International (Irrepressible campaign) and Reporters without borders etc. Above all I hope to present a coherent and well balanced report, which draws upon all the issues of Internet Censorship & which presents the reader with a good understanding of the these issues.
4. A description and assessment of research base. Primary sources. Secondary sources.
Much of my primary research will comprise of distributing Questionnaires, e-mails and letters to the appropriate persons. Case studies will be conducted into various countries to gain an understanding of the scale of internet censorship and the resulting penalties for braking set laws, be they an individual countries or international.
The secondary sources I will use will include books, videos, journals and articles on the internet. Although many articles, particularly on the internet may be bias or inaccurate, they will still be invaluable to my findings and understanding of the issue.
5. An indication of your preferred methodology and why it is appropriate. What academic approach will you choose that is best suited to the analysis, contextualisation and cultural critique of your subject?
Researching into this issue could be particularly difficult. Because this is such a profound issue for many people and because there are those who wish to distort the truth, individual agendas may play heavily on the information I find. Fortunately I have a background in Historical study and have had much experience of using primary and secondary sources. Therefore I am aware of the problems that bias and inaccurate information can cause, but should also be able to identify such issues.
When my research is complete, the academic approach I intend to use to analyse my findings will take the form of a philosophical discussion. I am concerned with the issue of Internet censorship and apart from just looking at the technical capabilities available to enforce this censorship and how to overcome them. I also intend to present an unbiased philosophical discussion, citing the works of key thinkers & philosophers. I think this would be particularity appropriate because it would allow me to gain a full understanding of the issues for and against internet censorship, before writing a conclusion on where I stand on the issue & presenting my finished project.
Furthermore, I intend to use appropriate law based methodology when I come to present my findings into the kinds of penalties issued for breaking censorship laws.
6. References to key thinkers/academics.
Isaiah Berlin (Political philosopher and Historian of ideas. 1909 - 1997).
Jeremy Waldron (Professor of law and philosophy at the New York University School of Law. 1953 - present).
Jonathan Wolff (Professor and Head of Department specialising in political philosophy at University College London. 1959 - present).
Bernard Williams (Professor of Philosophy at the University of Cambridge,1929 - 2003).
Ronald Dworkin (American legal philosopher, 1931 - present).
H. L. A. Hart (Legal philosopher, 1907 - 1992).
Jean-Jacques Rousseau (Philosopher of the Enlightenment, 1712 - 1778).
7. Indicative bibliography.
Freedom: An Introduction with Readings by Nigel Warburton
(Routledge, an imprint of Taylor & Francis Books Ltd. 14 Sep 2000).
The New Thought Police by Tammy Bruce
(Crown Publications. Jan 2003).
http://irrepressible.info/ (Amnesty International Campaign).
http://opennet.net/map/ (Internet Filtering Map).
http://www.rsf.org/ (Reporters without Boarders).
http://www.ispa.org.uk/ (The Internet Services Providers' Association. ISPA UK).
http://www.netfreedom.org/ (Free speech organisation).
http://www.eff.org/br/ (Electronic Frontier Foundation. Free speech organisation).
http://www.epic.org/crypto/ (Electronic Privacy Information Centre).
http://www.scripting.com/twentyFour/ (A Celebration of Free Speech on the Internet).
8. Additional information that is relevant.
Time willing, I would like to present my project not just in written form, but also in some kind of multi-media format. I wish to create either a video, e book, website or some other form of multi-media presentation. A written dissertation or journal may be appropriate for presenting my finding to an academic body, but I also wish to present my work in a form that is more accessible to a larger audience.
9. Any questions you may have for staff.
Having discussed this topic with S. Pope on the 30/10/06, I am happy that I have a credible and above all interesting proposal for a project. I will require further discourse soon, although I am happy to talk about my proposal at any time.
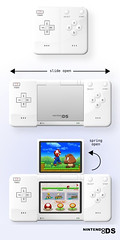
Re-Design of Nintendo DS Lite
Introduction
In a previous module I looked at the Nintendo DS Lite handheld gaming console and discussed the products usability and HCI issues. I now intend to take an user-centred approach, to redesign and make an improved prototype of this product. This article concludes with an evaluation of my redesigned prototype using Nielsen’s Discounted Usability Engineering method (‘DUE’).
Stage One - Redesign
To help identify user needs and requirements, I conducted a focus group with several friends who own or have used a Nintendo DS, as well as some who had never used one before. I wished to observe how people used the system and also hoped to identify any problems people had when using it. Furthermore, I was keen to learn what people thought was positive about the device and what could be done to improve it’s usability.
Several user issues and observations were identified. Firstly some users had sensitivity issues with both the D-Pad and the Touch Screen, meaning the user had to press down much harder in some games than others. There are also reliability issues with it’s built in Microphone; this is apparent in such games where the user is asked to interact with the game by blowing into the Microphone.
Some users commented that the DS is not exactly ergonomic. The rectangular base is reminiscent of a slightly smoothed NES controller, meaning you cannot wrap your palms all the way around it. However, whether in use with the normal controls, stylus or the thumb strap nobody complained of the device being uncomfortable to use. Nobody experienced any hand cramps which often plague some owners of small handheld devices who use them for prolonged periods.
On the positive side, I received an overwhelmingly positive response with regards to the devices usability & interface. To test usability and to see how effective the interface is, I asked all my participants to perform a simple task; switching the device on > loading a game > playing the game > switching the device off. Users reported that all the buttons on the interface are clearly marked and there is not too many either, with no unnecessary buttons that could confuse the user. As for the devices interface and menus, they are laid out and presented extremely well. There are large icons, with not too many options and diagrams to help reassure the user they are selecting the correct option. (A run down of the main Menu screen is presented below).
Top screen
1. Tool Bar - This displays the users name, the time on a 24 hour clock and the date.
2. Clock - Displaying the time.
3. Calendar - Displaying the date.
Bottom Touch Screen
4. Game Option File - Select this to play if a game is inserted. When a game is inserted, It displays the games name in text and also has a relevant picture.
5. Pictochat - This option file is for instant chat software which allows DS owners to communicate with each other, much like MSN messenger or Yahoo messenger.
6. DS Download Play - This option allows DS owners to download game patches off other DS owners so they can play each other wirelessly.
7. Game Pak - This option becomes visible when a game pak is inserted.
8. Settings - This option allows the user to change the devices settings, e.g. time, date, brightness, user information.
One innovation that was discussed was whether the inclusion of an analogue stick would be appropriate. However, as I discovered with the DS lower touch screen, it has the potential to offer similar functions as an analogue controller, but with greater interaction. PC shooters for example have had the advantage of mouse look, which gave a whole new dimension of immersion. But with the DS, games like Metroid Prime Hunters brings mouse look control into your pocket. With the default controls, the action plays out on the top screen and you use the touch screen and stylus to look around, whilst the D-Pad move you around and the triggers fire. So tasks preformed with conventional analogue sticks can also be preformed with greater effect with the DS stylus or thumb stick on the touch screen.
I also conducted internet based research to determine what other problems Nintendo have had with the production of the DS console. Even though the overall opinions are positive, there has been one or two manufacturing issues. There has been problems with the outside casing, with cracks appearing on the hinge nearest the left shoulder button. This problem is purely cosmetic and does not affect the game play or console whatsoever. Other users have reported dead or stuck pixels, although this is pretty common amongst TFT screens.
By conducting user testing I have learned that many of the problems the DS has is with it’s hardware and issues that arise after the manufacturing process. As for usability, the device has a clearly defined menu which is simple to navigate. It is similar to a mobile phone menu and incorporates similar design traits. Seeing there are no clear problems with the ergonomics or usability of the device, I have decided to focus my redesign work on the aesthetical appeal of the DS. I had the intention of creating a product which would incorporate all the features of the original, but would bring something new to the table and could still be incorporated into the existing Nintendo DS products line.
After completing several rough sketches, the concept I came up with was that of an expandable device, with a flip top screen (shown below). Apart from incorporating the new features of the expandable design with a flip screen, this design has the advantage of being smaller than the DS Lite when it is not in use. Meaning it takes up less room on your person and when in storage. Something else I think could be an interesting concept would be light up buttons (e.g. Red LED buttons). This feature could then be used for such games where the user is required to press a button at a certain time (e.g. Dance games).
Stage Two - User Testing
For this stage I was required to evaluate my redesigned prototype using Nielsen’s Discounted Usability Engineering method (‘DUE’). A method of user testing was difficult to realise with my redesign. As I found the DS has excellent user interaction qualities, I am only concerned with testing the ergonomics and aesthetical appeal of my redesign. I decided against creating a High-fidelity 3D prototype, predominately because I was not changing the Devices interface. Furthermore, you navigate the menus and select options through the touch screen, so a visual representation on a computer could be considered too artificial. Other factors for this decision include the high costs that would be involved, lack of time and lack of software. For these reasons Instead I created two Low-fidelity prototypes by printing off an image of my redesign and placing it onto blue foam; one of the console closed & another with the flip screen open. This approach has the advantage of being very cheap and quick to create, although it does not give me as much or as accurate information as a high-fidelity prototype would.
To conduct the trial, I asked each individual in the focus group to hold first the original Nintendo DS Lite console and then my two redesigned blue foam models. I then asked them to simulate performing various actions, so I could discover if the device was comfortable to use and that all the buttons were in a practical place.
Results
As I made my redesign with the original DS Lite in mind, I incorporated many of the originals key characteristics. I believe it is because of this reason that I received overall positive feedback. Users reported that they found the device to be more practical because it fitted into their pockets easily. Because the button layout is similar to the originals, nobody could see any user interaction issues. Furthermore, as the device is the same size as the original when it is in use, users reported no problems with the ergonomics of the new design. However, It was pointed out that my blue foam models did not effectively show how the device opened or how the flip-screen operated.
Nielsen’s Discounted Usability Engineering method (‘DUE’)
Simple and natural dialogue
Short precise langue is used to not confuse the user.
Speak the users’ language
A wide age-range of people would use this device. For this reason it is important that language is kept simple and to a minimum.
Minimise the users’ memory load
The amount of operations a user can perform are kept to a minimal, not to overburden the users memory load. This device is predominately used for playing games, one main menu screen means that options are kept to a minimum.
Consistency
The Language and Visuals used are consistent throughout the console. Information is presented in the same format and location throughout. This gives the users more confidence in using and exploring the system.
Feedback
Loading screens appear to reassure the user. They are never left in any doubt about the system state or what is happening. Fortunately the system does not have a long response time for the actions you ask it to perform, so in-depth user feedback is not needed.
Clearly marked exits
If a user makes a mistake or accesses a option they did not intend, exit boxes are always situated on the top right of the screen. This is consistent with the layout on many computer programs.
Shortcuts
Few shortcuts are provided because of the minimal operations you can perform on the device and because they are not needed in game play.
Good error messages
Error messages are a rarity. When they do appear, they are in plain and clear language, avoiding the use of obscure codes or technical jargon which could confuse the user.
Help and documentation
A short precise manual is provided that explains all the key operations effectively without overburdening the user.
Tuesday, October 17, 2006
Brief Three - U.C.I.
'Analyse an Arcade Machine.'
Having visited the UCI down Cardiff Bay, I have decided to write about an arcade machine I found there called 'Time Crisis 4.' Unfortunately when I went to the UCI there was not many visitors, so I ended up spending all my money to ensure I understood the HCI/Usability of the machine.
Observations & Interpretations
Time Crisis 4 is an interactive, one to two-player cooperative gun game. Specifically it is a first person Rail Shooter and is presented in a upright, twin cabinet (two screens). Players have the option to select either dual-player cooperative game play or dual single play in the same cabinet. I make this point because this use of multi-screens is highly innovative and original in an arcade machine.
As for the game itself, players are navigated through three stages & each stage consists of a prologue and three areas. The user is provided with a plastic light gun to interact with what is happening on the screen & has an in-game arsenal which includes a standard handgun, machine gun, shot gun and grenade. Players change weapons in the game by pulling the trigger while they hide (you hide by taking your feet off the foot pedal).
Forms of interaction
The main form of interaction the user has with this device is by shooting the enemies as they appear on the screen. The user is navigated automatically from scene to scene by the game. To assist players, they are guided through the three stages with the support of Voice Navigation, which comes from a speaker mounted on both players gun racks. The Voice Navigation provides players with instructions on selecting the appropriate weapons and timing their next move.
There is a also a foot pedal which players use to hide behind boxes and walls when the action becomes too intense. Players are also required to reload their weapons, like a real gun. This is achieved by aiming off screen and pulling the trigger button. In additional, players have the option to adjust the gun sight and select the blowback to on or off.
One other form of interaction Time Crisis 4 offers is the ability for players to control their fate, by offering multiple scenarios. Players are able to choose the direction they proceed at various points in the game; they can choose either right or left by pointing the gun at arrows located on the sides of the screen.
Is the interface design metaphorical?
The interface of this device is indeed metaphorical. The user is presented with a plastic imitation light gun and is placed in realistic gun fights, where they have to shoot and reload weapons and kill enemies in order to progress. The enemies are not passive and they fire back at the player, symbolised by red flashing holes when hit.
How do the exhibits in the UCI differ from those in Techniquest?
The exhibits in the UCI are all entertainment based, while the devices in Techniquest have an emphasis on education. The arcade machines in the UCI are intended to make money, so it is reasonable to assume they are aimed at young people with disposable income. These machines earn money every play, so the longer they keep the user entertained, the more money they make. This differs from Techniquest, where you pay upon entering to use all the machines as many times as you like.
Please click link for additional photos http://www.flickr.com/photos/64946738@N00/sets/72157594333222322/show/